After I earlier this week did the pleasant discovery that and how-to an external can be involved as presenter in a Teams Live Event, I decided to test whether same is possible within Yammer Live Event production. That could work, as Yammer Live Event production can be via Teams. The short report out: Yes, also this proofs possible!
The enabling preconditions (external known as Azure AD B2B guest in organizing Teams, and switched in Teams App to the organizing tenant) and steps are comparable with involving an external in Teams Live Event presentation, although few significant differences:
- In the organizing tenant, schedule in producer / organizer role within Yammer a new Live Event. Crucial also here is to select that the production will be done 'via Teams', not 'via External app or device'. In this step in Yammer UI, do not try to invite the external as presenter as that fails: Yammer does not allow the external to be resolved (unless you have enabled external access of the Yammer channel itself)
- In Yammer of the organizing tenant, navigate to the scheduled Live Event and click on "Produce (Open in Teams)". After the Yammer Live Event is opened in Teams App, click 'Join now'.
- Crucial step: in the internal Teams meeting of the Live Event, click on the button 'Show participants'. And in the Teams meeting context, invite the external person via his/her external guest identity;


- Under the preconditions that the external person is active in Teams, and switched there to the organizing tenant, (s)he receives a request notification to join in the internal Teams meeting of the Yammer Live Event

- The invited external accepts the invite to join this active Teams Meeting, and can then share content + video in the meeting context of the Yammer Live Event;

- The Yammer Live Event producer waits in the Teams Live Event production room until the external person has joined, and shares content in the internal meeting of the Live Event. When visible, the producer is in control to select content and/or video of this external presenter in the queue;
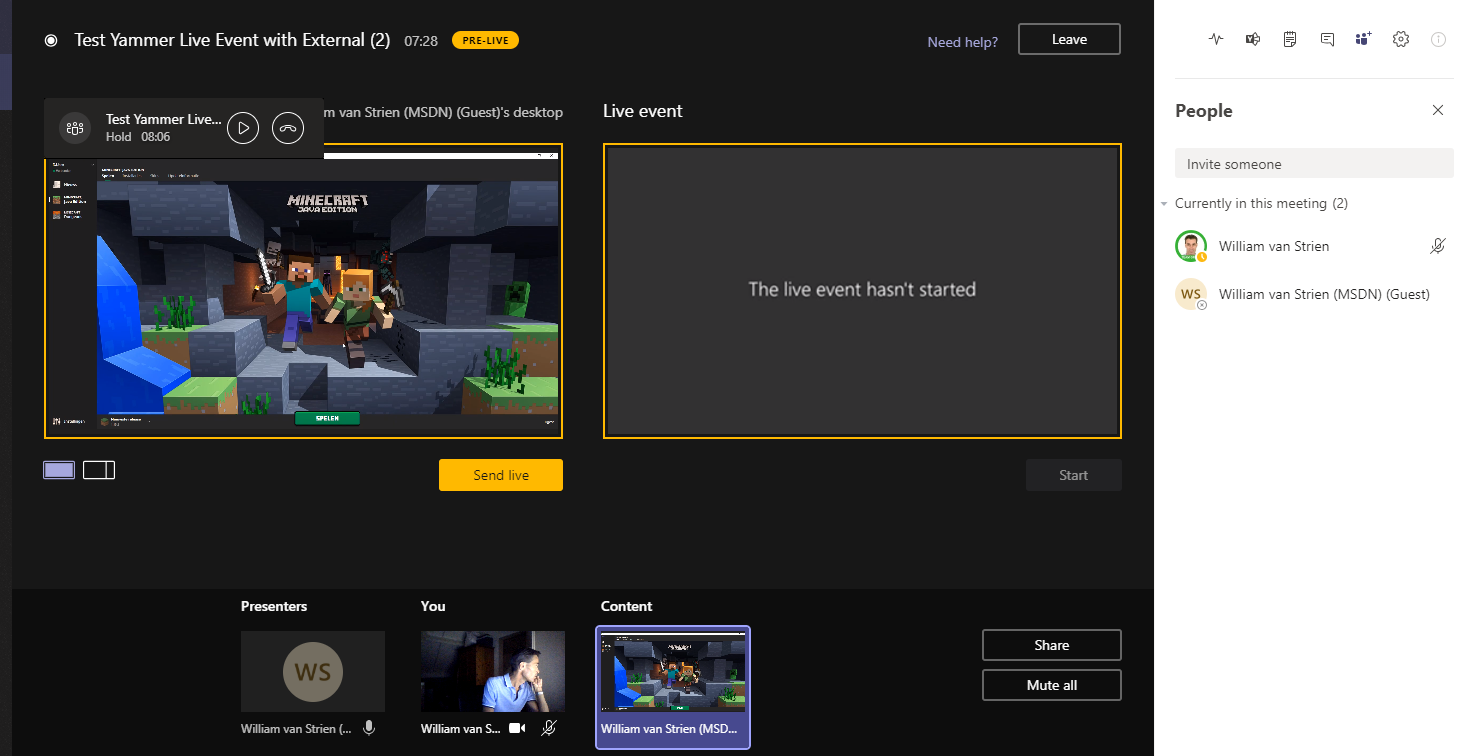
- The producer pushes from the queue to live, and starts the Live Event;
- The audience of the Yammer Live Event see the content and/or video of the external presenter;

- And audience on-the-go can watch the external presenter in the Yammer Mobile App;